Identification of induced information for personalized recommendations based on knowledge graph
-
摘要:
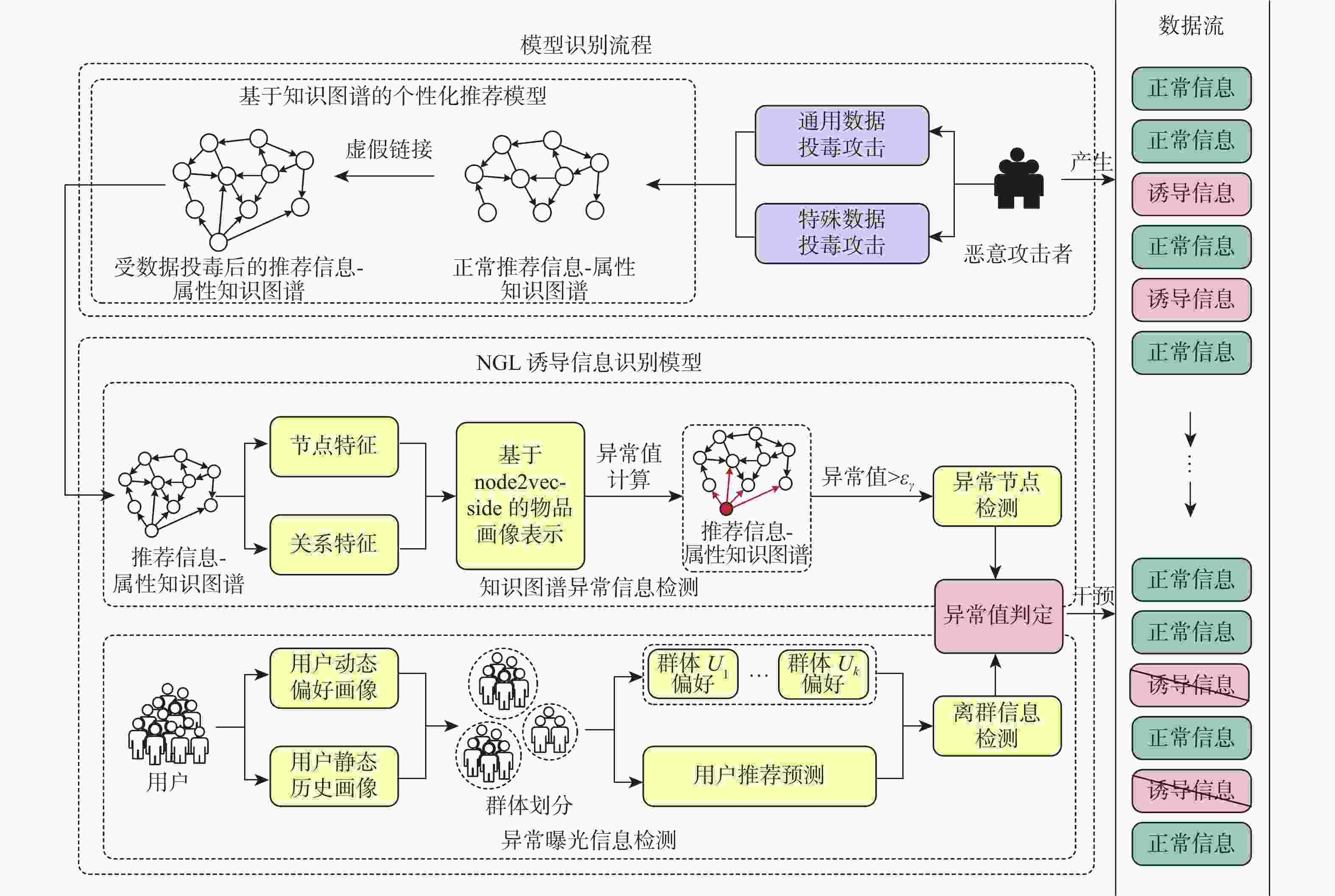
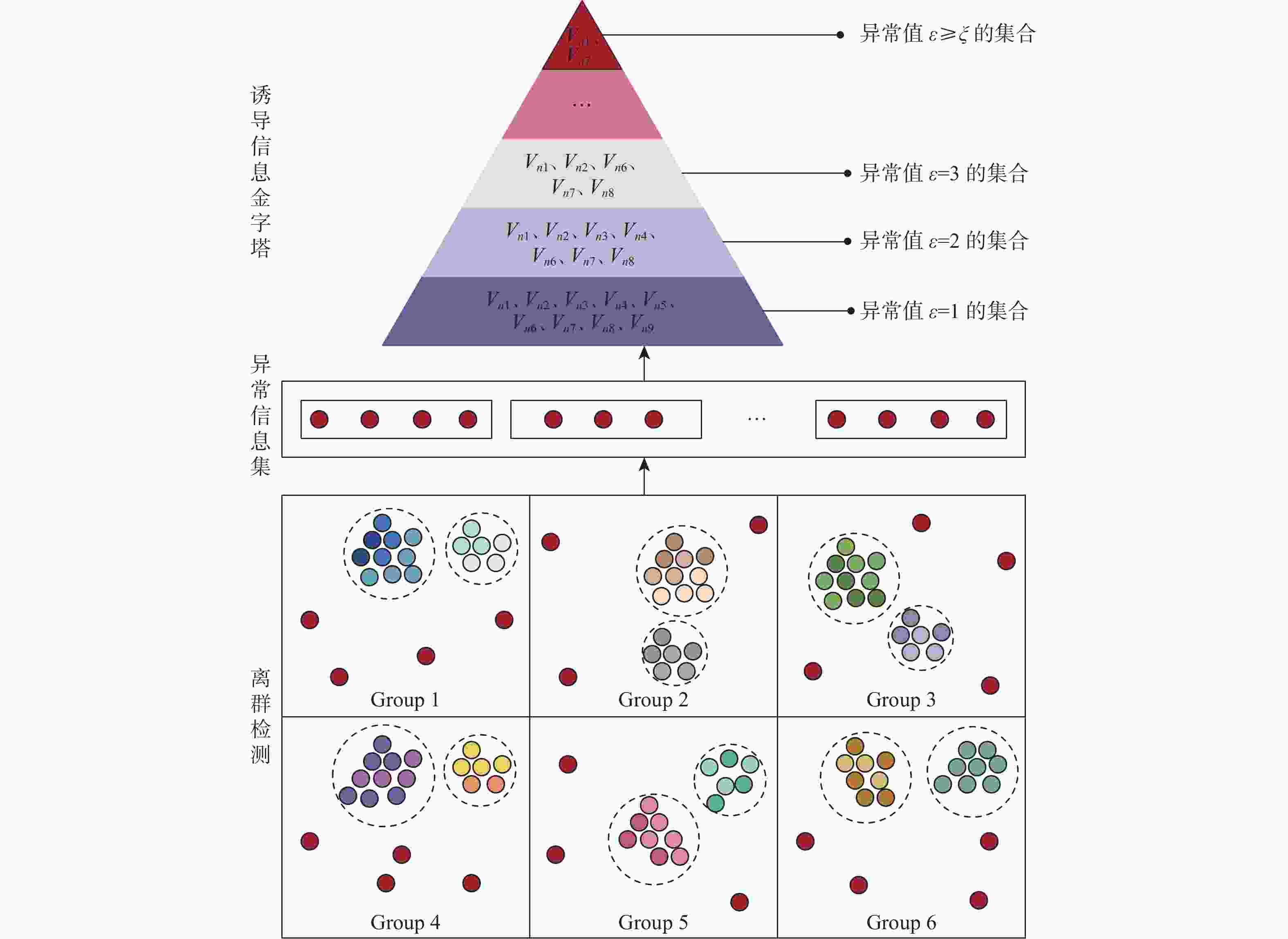
互联网信息服务算法推荐管理,是构建智能信息时代国家互联网治理体系的重要手段。个性化推荐算法是互联网信息服务算法推荐的重要技术之一,知识图谱在个性化推荐算法中有广泛应用,同时知识图谱和推荐算法容易受到攻击者的数据投毒攻击,进而影响推荐结果,造成诱导信息传播。当前,针对此类诱导信息识别缺少有效的模型,基于此开展诱导信息识别模型研究,在对用户历史行为记录及用户偏好的演化过程进行分析的基础上,研究基于用户兴趣与群体感知的诱导信息检测方法,对相似用户群体历史偏好进行群体偏好建模,对具有共性特征的群体内异常曝光的信息进行离群点分析,构建集node2vec-side 物品表示、高斯混合模型(GMM)群体划分和 LUNAR 异常检测的诱导信息识别模型NGL,从用户偏好变化与推荐结果演变推理实现诱导信息识别。在RippleNet和MKR推荐系统上进行诱导信息识别实验,结果表明:NGL模型优于现有的异常检测模型。
Abstract:In the age of intelligent information, managing the recommendations of Internet information service algorithms is a crucial step in creating a national Internet governance framework. Personalized recommendation algorithm is one of the important technologies for Internet information service algorithm recommendation. The knowledge graph is widely used in personalized recommendation algorithms. At the same time, the knowledge graph and recommendation algorithm are vulnerable to data poisoning attacks by attackers, which in turn affects the recommendation results and induces information dissemination. There is a lack of effective models for identifying this type of induced information. Based on this, this article conducts research on the induced information identification model. Based on the analysis of user historical behavior records and the evolution process of user preferences, we study induction based on user interests and group perception. Information detection method, perform group preference modeling on the historical preferences of similar user groups, perform outlier analysis on abnormally exposed information within groups with common characteristics, and construct set node2vec-side item representation, GMM group division, and LUNAR induction for anomaly detection User preference modifications and recommendation result evolution reasoning are the basis for the realization of induced information recognition by the information recognition model NGL (Induced information detection model that incorporates node2vec-side item representation, GMM group division, and LUNAR, NGL). Induced information recognition experiments were conducted on RippleNet and MKR recommendation systems. The results show that the NGL model proposed in this article is better than the existing anomaly detection model.
-
表 1 推荐系统数据集统计信息
Table 1. Statistics for recommended system datasets
数据集 用户数 项目数 交互数 三元组数 MovieLens-1M 6 036 2 445 753 772 1 241 995 Book-Crossing 17 860 14 967 139 746 151 500 Last.FM 1 872 3 846 42 346 15 518 表 2 通用数据投毒攻击参数
Table 2. General data poisoning attack parameter
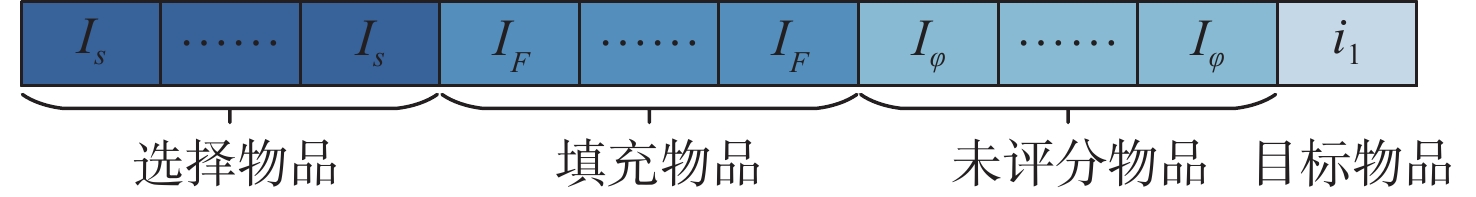
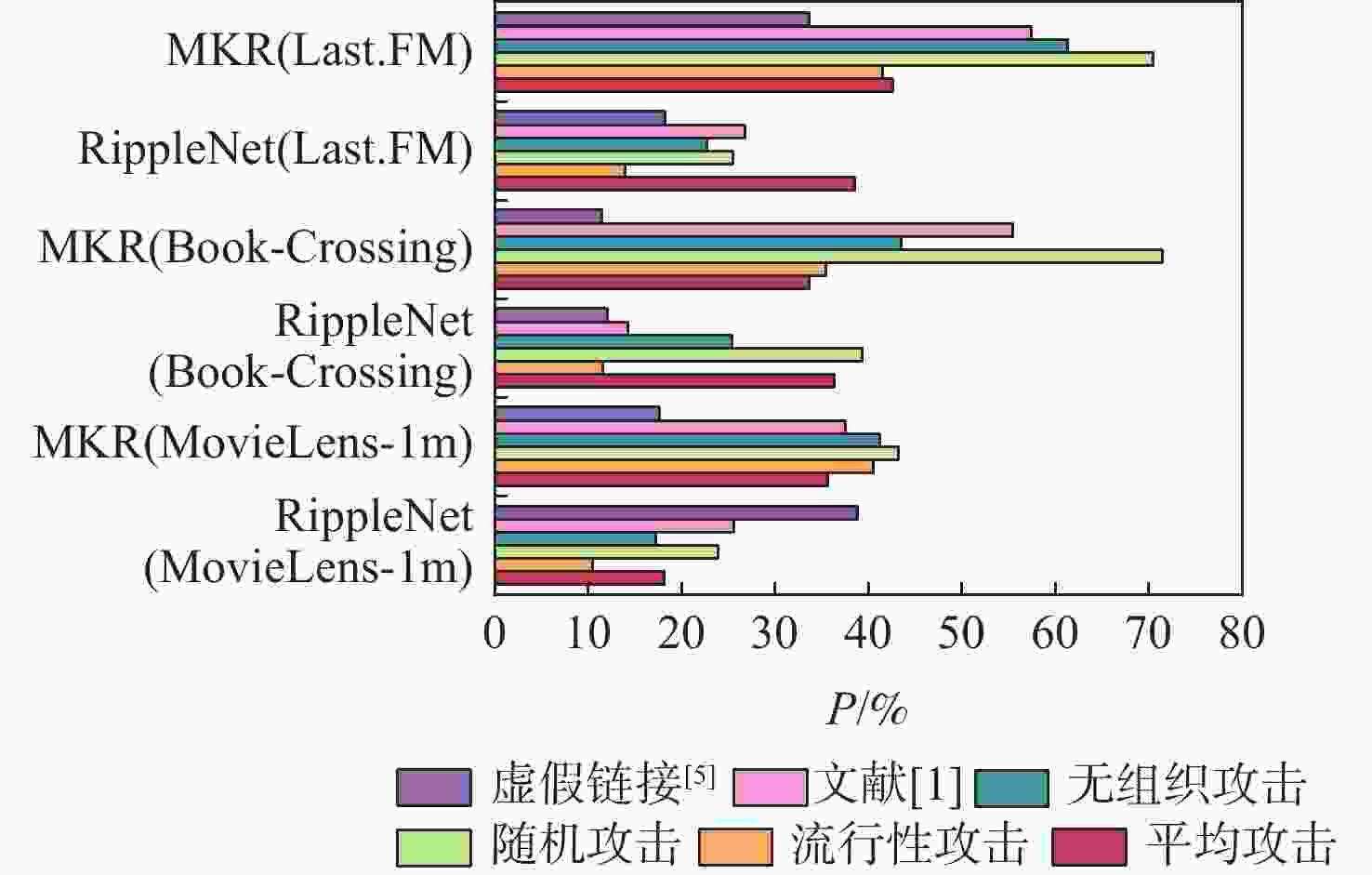
数据集 攻击规模 填充规模 选择规模 MovieLens-1M 0.15 0.015 0.05 Book-Crossing 0.2 0.015 0.1 Last.FM 0.2 0.015 0.1 表 3 推荐信息诱导传播对比
Table 3. Comparison of recommendation message induced propagation
% 数据集 攻击 RippleNet MKR Rhit@1 Rhit@3 Rhit@5 Rhit@10 Rhit@1 Rhit@3 Rhit@5 Rhit@10 MovieLens-1M 无攻击 0.014 4 0.044 1 0.070 6 0.137 1 0.003 5 0.025 9 0.055 7 0.138 9 平均攻击 0.043 5 0.145 2 0.251 3 0.512 5 0.324 2 0.576 0 0.654 2 0.963 7 流行性攻击 0.031 1 0.102 7 0.190 9 0.401 6 0.330 7 0.822 0 1.293 6 2.220 5 随机攻击 0.024 8 0.104 5 0.197 7 0.414 3 0.259 2 0.835 3 1.482 8 2.738 6 无组织攻击 0.049 8 0.153 9 0.248 5 0.438 6 0.229 4 0.689 3 1.123 3 2.180 3 文献[1] 0.029 8 0.126 1 0.240 3 0.468 5 0.152 1 0.476 8 0.715 2 1.267 5 虚假链接[5] 0.098 5 0.349 4 0.582 4 1.146 1 0.006 3 0.026 3 0.090 3 0.290 0 Book-Crossing 无攻击 0.004 9 0.016 6 0.028 5 0.058 5 0.000 0 0.000 0 0.000 0 0.000 0 平均攻击 0.043 3 0.074 7 0.118 0 0.202 3 0.024 8 0.605 5 0.866 1 1.167 3 流行性攻击 0.004 8 0.033 7 0.046 4 0.084 4 0.000 0 0.040 3 0.037 4 0.371 1 随机攻击 0.029 1 0.067 9 0.089 9 0.162 1 0.626 9 1.587 1 2.247 3 3.366 2 无组织攻击 0.011 2 0.041 8 0.063 0 0.119 8 0.048 5 0.083 4 0.142 6 2.116 4 文献[1] 0.006 7 0.029 5 0.051 2 0.117 1 0.131 7 0.716 2 1.650 3 3.405 9 虚假链接[5] 0.007 9 0.019 6 0.033 8 0.092 9 0.000 0 0.024 8 0.023 0 0.065 3 Last.FM 无攻击 0.018 2 0.089 7 0.130 3 0.242 5 0.000 0 0.000 0 0.000 0 0.027 5 平均攻击 0.056 5 0.165 2 0.312 7 0.731 3 0.138 3 0.418 2 0.720 9 1.488 7 流行性攻击 0.046 9 0.207 6 0.280 1 0.572 5 0.051 8 0.103 6 0.145 5 0.345 2 随机攻击 0.031 4 0.081 2 0.157 0 0.392 5 0.244 6 0.971 0 1.287 0 2.655 4 无组织攻击 0.035 2 0.094 4 0.158 6 0.361 6 0.313 5 0.884 7 1.455 6 2.947 7 文献[1] 0.051 6 0.185 8 0.364 1 0.827 9 0.039 0 0.099 3 0.192 7 0.459 9 虚假链接[5] 0.061 4 0.147 6 0.239 0 0.537 8 0.008 2 0.032 1 0.188 6 0.418 7 表 4 白盒测试中NGL参数设置
Table 4. NGL parameter settings in white-box testing
数据集 n_cluster n epsilon d top_N MovieLens-1M 15 30 0.01 48 10 Book-Crossing 10 20 0.1 64 10 Last.FM 15 20 0.1 48 25 表 5 RippleNet中MovieLens-1m诱导识别结果
Table 5. Induced recognition results of MovieLens-1m in RippleNet
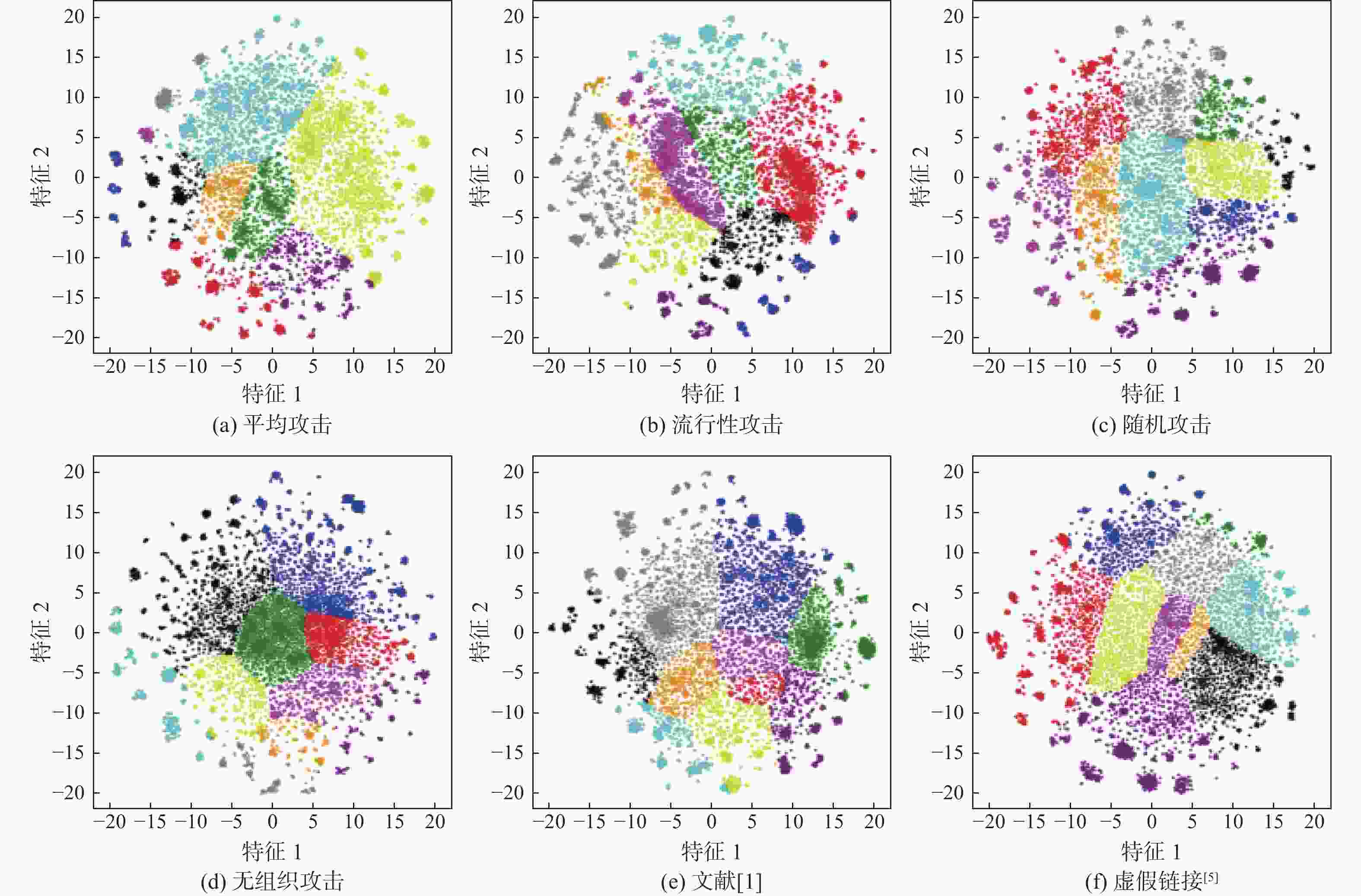
模型 P/% AUC 平均攻击 流行性攻击 随机攻击 无组织攻击 文献[1] 虚假链接[5] 平均攻击 流行性攻击 随机攻击 无组织攻击 文献[1] 虚假链接[5] ABOD 6.45 8.33 14.15 9.26 9.28 5.28 61.69 57.66 65.43 63.27 55.63 59.40 KNN 10.08 8.85 14.58 13.79 7.03 8.06 59.68 59.05 62.72 62.14 59.45 60.75 INNE 6.68 7.14 11.94 8.91 7.41 9.15 57.31 61.95 63.79 61.28 56.11 58.61 MCD 6.48 6.04 19.25 14.29 8.35 7.58 61.73 55.40 65.93 65.78 58.67 60.90 COPOD 3.18 6.61 16.34 9.51 9.88 12.51 56.73 59.26 60.66 57.49 68.89 72.75 LUNAR 7.69 8.27 22.49 12.13 7.79 10.81 63.31 61.81 66.82 63.51 61.19 62.45 ECOD 3.26 4.35 14.82 10.53 10.53 16.56 58.43 63.57 65.44 58.19 65.31 71.84 I Forest 2.42 6.25 11.48 8.97 7.69 13.09 57.80 59.64 61.97 58.41 62.25 66.20 HBOS 3.50 7.18 9.69 8.11 7.41 14.16 57.96 60.28 62.81 58.71 63.27 68.00 ALAD 3.29 6.12 6.82 8.57 11.84 15.93 59.69 55.88 59.12 56.47 62.57 69.73 ROD 1.85 5.71 6.77 4.86 12.71 14.29 55.27 56.71 53.55 61.76 72.46 NGL 18.16 10.53 23.91 17.24 25.56 38.81 71.65 65.13 71.04 68.08 73.90 79.89 表 6 RippleNet中Book-Crossing诱导识别结果
Table 6. Induced recognition results of Book-Crossing in RippleNet
模型 P/% AUC 平均攻击 流行性攻击 随机攻击 无组织攻击 文献[1] 虚假链接[5] 平均攻击 流行性攻击 随机攻击 无组织攻击 文献[1] 虚假链接[5] ABOD 21.40 1.72 16.24 5.12 8.80 82.68 62.04 77.18 62.11 64.34 KNN 27.09 3.30 16.65 17.84 9.83 0.35 83.55 57.96 71.89 76.57 66.44 52.98 INNE 16.13 7.52 9.28 14.28 7.91 1.76 78.49 61.20 65.20 70.70 60.26 57.18 MCD 21.94 3.08 34.25 4.49 0.99 3.74 72.81 66.84 84.39 59.32 56.29 55.16 COPOD 8.82 1.36 2.31 7.24 6.13 3.08 63.46 56.75 65.88 73.81 58.01 LUNAR 22.80 3.33 18.45 8.22 7.67 6.64 72.23 66.19 75.32 71.65 69.13 59.54 ECOD 15.49 2.15 4.87 8.35 7.06 0.86 73.50 58.94 63.80 66.31 65.80 58.29 I Forest 15.58 2.45 11.31 15.25 8.23 0.27 64.84 57.63 67.99 73.88 71.06 55.95 HBOS 14.84 2.04 5.41 8.65 6.25 1.44 63.09 54.70 64.86 66.28 72.92 55.22 ALAD 2.62 3.11 3.95 3.22 1.65 2.81 59.19 56.01 57.51 57.51 56.51 60.87 ROD 14.24 4.47 5.26 7.16 7.59 2.50 61.33 57.51 58.02 62.63 64.38 56.99 NGL 36.32 11.58 39.36 25.43 14.23 12.05 88.64 74.23 89.41 84.79 78.22 75.11 表 7 RippleNet中Last.FM诱导识别结果
Table 7. Induced recognition results of Last.FM in RippleNet
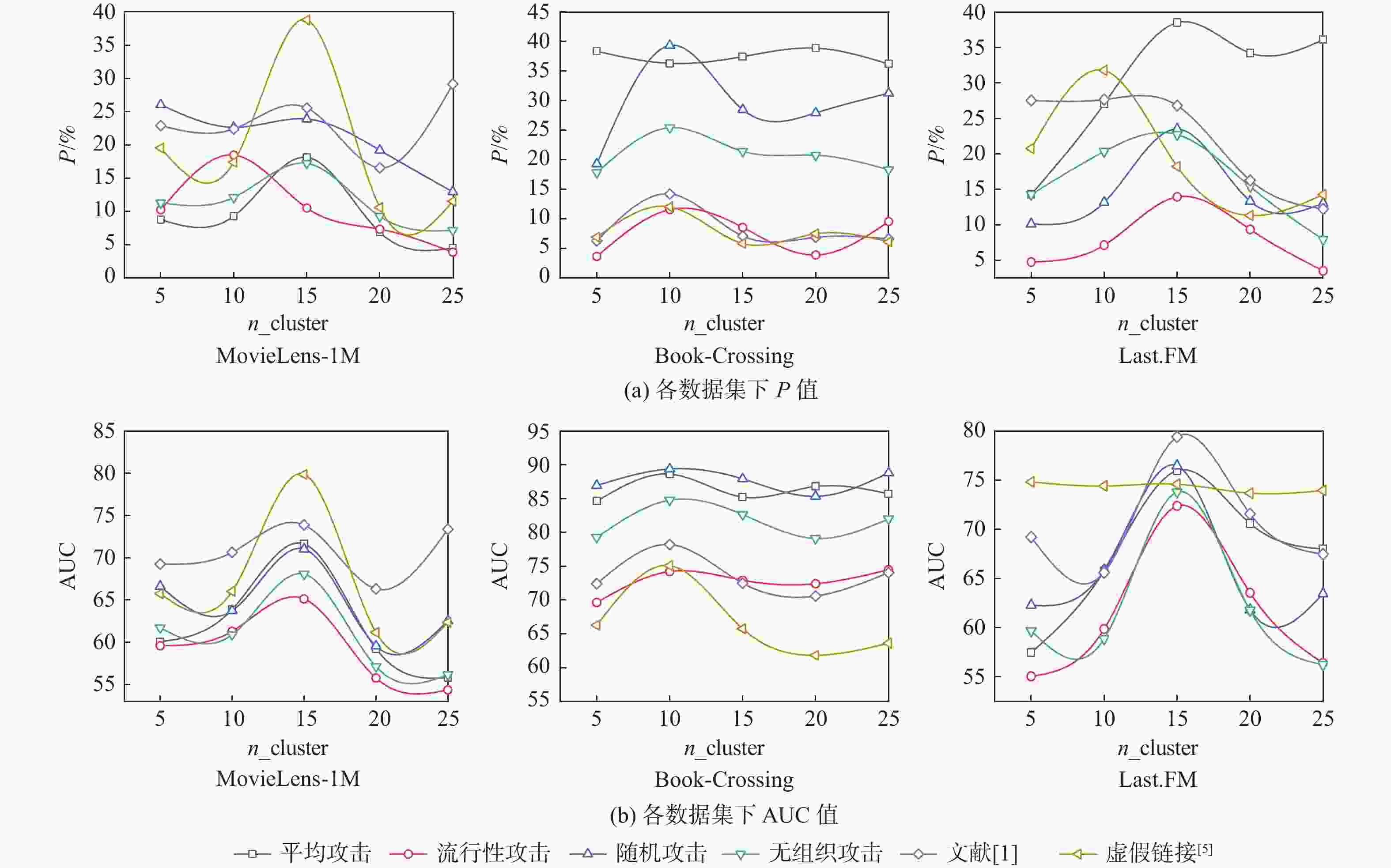
模型 P/% AUC 平均攻击 流行性攻击 随机攻击 无组织攻击 文献[1] 虚假链接[5] 平均攻击 流行性攻击 随机攻击 无组织攻击 文献[1] 虚假链接[5] ABOD 10.94 7.66 7.33 4.43 6.02 2.48 57.51 63.18 65.90 57.62 54.58 KNN 14.60 10.68 14.21 20.34 6.03 8.27 60.18 63.41 68.42 66.61 57.62 58.16 INNE 7.79 7.12 12.64 8.32 9.82 6.14 64.88 62.55 61.17 57.29 72.18 54.95 MCD 9.55 6.32 6.06 6.89 4.83 7.40 55.07 59.80 64.19 57.41 55.63 55.71 COPOD 21.10 3.29 6.58 4.95 20.55 13.09 70.13 55.75 62.05 76.69 61.58 LUNAR 11.42 9.08 17.91 12.05 9.33 7.84 67.72 63.16 71.10 63.19 62.15 54.06 ECOD 11.11 10.91 8.07 13.55 12.22 8.29 65.82 59.15 62.76 60.49 75.01 55.62 I Forest 14.38 10.57 7.20 12.31 11.44 8.04 65.57 61.88 61.84 58.43 74.59 56.32 HBOS 22.89 9.34 7.81 10.61 13.78 7.68 69.16 58.91 61.17 58.02 72.03 56.18 ALAD 9.85 3.21 8.40 8.91 5.17 5.82 69.23 54.03 60.83 57.09 55.89 54.84 ROD 14.15 8.24 6.19 6.90 14.18 3.70 72.23 59.03 61.90 56.49 69.63 NGL 38.51 13.94 25.51 22.73 26.81 18.23 75.98 72.38 76.47 73.79 79.41 74.59 表 8 黑盒测试中NGL参数设置
Table 8. NGL parameter settings in black-box testing
数据集 n_cluster n epsilon d top_N MovieLens-1M 10 30 0.05 16 10 Book-Crossing 10 20 0.01 16 25 Last.FM 10 20 0.1 16 25 表 9 MKR中MovieLens-1m诱导识别结果
Table 9. Induced recognition results of MovieLens-1m in MKR
模型 P/% AUC 平均攻击 流行性攻击 随机攻击 无组织攻击 文献[1] 虚假链接[5] 平均攻击 流行性攻击 随机攻击 无组织攻击 文献[1] 虚假链接[5] ABOD 14.29 34.91 7.14 13.80 14.71 3.85 60.90 78.44 53.41 62.76 66.49 55.20 KNN 29.41 35.27 4.76 24.96 23.61 4.95 59.45 79.60 53.10 62.83 68.12 56.73 INNE 15.79 39.57 33.91 23.22 28.92 3.70 71.58 82.02 76.31 74.89 75.97 58.08 MCD 6.40 34.86 4.08 6.81 22.65 1.63 56.63 79.08 56.11 63.95 72.86 COPOD 5.04 5.10 3.27 4.77 19.26 3.13 60.72 56.12 57.15 62.00 67.34 55.01 LUNAR 32.74 38.42 14.29 35.71 29.63 3.86 66.84 81.93 58.68 62.75 71.39 57.39 ECOD 7.41 15.79 1.82 2.17 23.08 7.42 65.83 63.51 60.21 65.30 58.26 I Forest 5.44 37.21 34.49 7.14 18.37 2.44 62.24 77.18 77.72 72.70 74.07 55.64 HBOS 7.69 22.71 6.46 1.99 21.43 4.08 57.65 69.28 63.26 69.12 66.73 56.40 ALAD 11.23 17.24 19.59 12.84 23.03 3.76 69.91 67.55 71.60 67.32 69.40 56.91 ROD 7.14 3.27 2.56 5.40 15.79 2.04 70.24 55.10 65.05 68.88 NGL 35.71 40.55 43.19 41.22 37.54 18.79 77.95 82.47 81.97 83.14 78.84 70.35 表 10 MKR中Book-Crossing诱导识别结果
Table 10. Induced recognition results of Book-Crossing in MKR
模型 P/% AUC 平均攻击 流行性攻击 随机攻击 无组织攻击 文献[1] 虚假链接[5] 平均攻击 流行性攻击 随机攻击 无组织攻击 文献[1] 虚假链接[5] ABOD 29.76 9.67 29.15 9.43 10.74 2.31 75.56 64.12 79.54 65.10 62.71 58.24 KNN 27.49 24.77 54.72 29.58 14.93 5.44 75.42 75.57 88.89 80.69 62.26 54.86 INNE 22.07 17.49 34.72 24.10 41.26 1.96 67.35 71.48 85.07 79.32 83.23 MCD 16.13 6.00 57.81 10.48 16.05 9.81 61.40 58.90 89.44 64.37 80.21 61.91 COPOD 14.90 20.97 47.78 9.09 51.01 4.05 64.66 72.85 86.84 69.53 85.59 53.43 LUNAR 29.42 27.46 46.67 34.03 13.62 5.99 74.69 79.11 82.72 86.95 73.20 59.87 ECOD 8.46 20.76 36.11 7.23 48.27 3.63 62.00 70.38 80.97 73.32 77.74 55.78 I Forest 18.23 14.72 49.81 36.29 50.50 4.45 66.03 65.37 86.67 85.05 82.65 54.39 HBOS 14.05 13.84 43.59 2.67 44.76 1.44 63.44 65.74 82.04 63.71 83.43 ALAD 3.43 28.89 18.78 2.38 6.44 5.89 59.71 82.39 73.48 61.81 60.02 57.51 ROD 4.22 11.08 31.11 6.27 1.87 1.03 68.53 71.23 82.75 77.54 NGL 33.69 35.48 71.45 43.55 55.47 11.46 86.69 87.64 96.88 91.08 89.27 82.58 表 11 MKR中Last.FM诱导识别结果
Table 11. Induced recognition results of Last.FM in MKR
模型 P/% AUC 平均攻击 流行性攻击 随机攻击 无组织攻击 文献[1] 虚假链接[5] 平均攻击 流行性攻击 随机攻击 无组织攻击 文献[1] 虚假链接[5] ABOD 12.99 26.67 45.15 16.59 25.81 17.86 69.46 71.09 74.30 67.82 67.30 71.99 KNN 20.18 30.21 55.82 29.64 36.82 14.29 75.30 66.28 79.13 72.15 64.63 72.69 INNE 22.91 32.91 46.41 14.48 51.73 13.64 74.68 65.59 73.79 66.38 78.82 68.02 MCD 9.09 29.72 59.47 17.20 46.81 6.90 56.33 70.26 87.93 74.26 74.62 61.04 COPOD 17.10 8.71 55.34 5.35 20.93 4.77 68.99 64.58 86.89 62.23 59.47 62.54 LUNAR 27.53 32.81 57.17 30.33 48.15 17.24 79.38 77.61 85.59 76.48 75.63 71.69 ECOD 10.73 17.59 49.93 4.04 19.15 4.17 71.64 68.48 82.60 59.61 58.46 63.44 I Forest 37.04 24.54 61.95 54.26 49.46 7.90 78.01 71.47 87.48 79.63 77.80 62.85 HBOS 33.91 9.09 60.90 53.25 28.29 4.57 79.27 63.42 87.31 78.83 59.57 65.48 ALAD 18.72 18.89 29.17 41.67 42.55 9.92 72.29 68.82 66.83 73.28 77.26 62.14 ROD 14.81 7.11 10.37 8.46 30.37 3.63 71.85 67.23 69.75 65.44 72.54 66.97 NGL 42.62 41.57 70.52 61.35 57.46 33.68 81.26 79.34 92.06 85.49 83.95 95.12 表 12 不同部分对模型识别结果的影响
Table 12. Impact of different parts on model recognition results
数据集 模块 P/% AUC 群体划分 异常节点检测 无组织攻击 文献[1] 虚假链接[5] 无组织攻击 文献[1] 虚假链接[5] MovieLens-1M − − 12.91 7.91 11.08 63.88 61.87 62.51 √ − 16.63 25.40 13.11 68.05 73.03 66.67 √ √ 17.25 25.23 38.52 68.93 73.47 79.78 Book-Crossing − − 8.47 8.62 7.32 72.56 69.72 59.97 √ − 24.75 13.92 7.99 84.31 77.23 60.67 √ √ 25.43 14.23 12.05 84.79 78.22 75.11 Last.FM − − 12.05 9.33 7.84 63.19 62.15 54.06 √ − 22.38 26.08 9.90 73.59 78.46 58.76 √ √ 22.73 26.81 18.23 73.79 79.41 74.59 -
[1] ZHANG H T, TIAN C X, LI Y L, et al. Data poisoning attack against recommender system using incomplete and perturbed data[C]// Proceedings of the 27th ACM SIGKDD Conference on Knowledge Discovery & Data Mining. New York: ACM, 2021: 2154-2164. [2] ZHANG H T, ZHENG T H, GAO J, et al. Data poisoning attack against knowledge graph embedding[EB/OL]. (2019-06-24)[2023-05-04]. http://doi.org/10.48550/arXiv.1904.12052. [3] BHARDWAJ P, KELLEHER J, COSTABELLO L, et al. Poisoning knowledge graph embeddings via relation inference patterns[EB/OL]. (2021-11-11)[2023-05-04]. http://doi.org/48550/arXiv.2111.06345. [4] BHARDWAJ P, KELLEHER J, COSTABELLO L, et al. Adversarial attacks on knowledge graph embeddings via instance attribution methods[EB/OL]. (2021-11-04)[2023-05-04]. http://doi.org/10.48550/arXiv.2111.03120. [5] WU Z W, CHEN C T, HUANG S H. Poisoning attacks against knowledge graph-based recommendation systems using deep reinforcement learning[J]. Neural Computing and Applications, 2022, 34(4): 3097-3115. doi: 10.1007/s00521-021-06573-8 [6] AKTUKMAK M, YILMAZ Y, UYSAL I. Quick and accurate attack detection in recommender systems through user attributes[C]// Proceedings of the 13th ACM Conference on Recommender Systems. New York: ACM, 2019: 348-352. [7] CAI H Y, ZHANG F Z. Detecting shilling attacks in recommender systems based on analysis of user rating behavior[J]. Knowledge-Based Systems, 2019, 177: 22-43. doi: 10.1016/j.knosys.2019.04.001 [8] ZHANG S J, YIN H Z, CHEN T, et al. GCN-based user representation learning for unifying robust recommendation and fraudster detection[C]// Proceedings of the 43rd International ACM SIGIR Conference on Research and Development in Information Retrieval. New York: ACM, 2020: 689-698. [9] YANG L, NIU X X. A genre trust model for defending shilling attacks in recommender systems[J]. Complex & Intelligent Systems, 2023, 9(3): 2929-2942. [10] CHEN X, DENG X, HUANG C S, et al. Detection of trust shilling attacks in recommender systems[J]. IEICE Transactions on Information and Systems, 2022, E105.D(6): 1239-1242. doi: 10.1587/transinf.2021EDL8094 [11] ZHANG F Z, ZHANG Z N, ZHANG P, et al. UD-HMM: an unsupervised method for shilling attack detection based on hidden Markov model and hierarchical clustering[J]. Knowledge-Based Systems, 2018, 148: 146-166. doi: 10.1016/j.knosys.2018.02.032 [12] ZHANG F Z, QU Y Q, XU Y S, et al. Graph embedding-based approach for detecting group shilling attacks in collaborative recommender systems[J]. Knowledge-Based Systems, 2020, 199: 105984. doi: 10.1016/j.knosys.2020.105984 [13] HAO Y J, MENG G Y, WANG J, et al. A detection method for hybrid attacks in recommender systems[J]. Information Systems, 2023, 114: 102154. doi: 10.1016/j.is.2022.102154 [14] JENY J R V, SOWMYA R, KIRAN G S, et al. Shilling attack detection system for online recommenders[C]//Proceedings of the 2022 International Conference on Inventive Computation Technologies. Piscataway: IEEE Press, 2022: 988-992. [15] GROVER A, LESKOVEC J. node2vec: scalable feature learning for networks[EB/OL]. (2016-07-03)[2023-06-25]. http://doi.org/10.48550/arXiv.1607.00653. [16] WANG H, ZHANG F, WANG J, et al. RippleNet: propagating user preferences on the knowledge graph for recommender systems[C]// Proceedings of the 27th ACM Interna-tional Conference on Information and Knowledge Manage-ment. New York: ACM, 2018: 417-426. [17] ZHANG C J, ZENG A. Behavior patterns of online users and the effect on information filtering[J]. Physica A: Statistical Mechanics and its Applications, 2012, 391(4): 1822-1830. doi: 10.1016/j.physa.2011.09.038 [18] AZMEDROUB B, OUARZEDDINE M. Polarimetric SAR images clustering with Gaussian mixtures model[C]//Proceedings of the 2015 3rd International Conference on Control, Engineering & Information Technology. Piscataway: IEEE Press, 2015: 1-5. [19] GOODGE A, HOOI B, NG S K, et al. LUNAR: unifying local outlier detection methods via graph neural networks[J]. Proceedings of the AAAI Conference on Artificial Intelligence, 2022, 36(6): 6737-6745. doi: 10.1609/aaai.v36i6.20629 [20] WANG H W, ZHANG F Z, ZHAO M, et al. Multi-task feature learning for knowledge graph enhanced recommendation[C]//Proceedings of the The World Wide Web Conference. New York: ACM, 2019: 2000-2010. [21] KRIEGEL H P, SCHUBERT M, ZIMEK A. Angle-based outlier detection in high-dimensional data[C]// Proceedings of the 14th ACM SIGKDD International Conference on Knowledge Discovery and Data Mining. New York: ACM, 2008: 444-452. [22] RAMASWAMY S, RASTOGI R, SHIM K. Efficient algorithms for mining outliers from large data sets[C]// Proceedings of the 2000 ACM SIGMOD International Conference on Management of Data. New York: ACM, 2000: 427-438. [23] BANDARAGODA T R, TING K M, ALBRECHT D, et al. Isolation-based anomaly detection using nearest-neighbor ensembles[J]. Computational Intelligence, 2018, 34(4): 968-998. doi: 10.1111/coin.12156 [24] LIU F T, TING K M, ZHOU Z H. Isolation forest[C]//Processings of the 2008 Eighth IEEE International Conference on Data Mining. Piscataway: IEEE Press, 2008: 413-422. [25] HARDIN J, ROCKE D M. Outlier detection in the multiple cluster setting using the minimum covariance determinant estimator[J]. Computational Statistics & Data Analysis, 2004, 44(4): 625-638. [26] LI Z, ZHAO Y, HU X Y, et al. ECOD: unsupervised outlier detection using empirical cumulative distribution functions[J]. IEEE Transactions on Knowledge and Data Engineering, 2022, 35(12): 12181-12193. [27] ALMARDENY Y, BOUJNAH N, CLEARY F. A novel outlier detection method for multivariate data[J]. IEEE Transactions on Knowledge and Data Engineering, 2022, 34(9): 4052-4062. doi: 10.1109/TKDE.2020.3036524 [28] LI Z, ZHAO Y, BOTTA N, et al. COPOD: copula-based outlier detection[C]//Proceedings of the 2020 IEEE International Conference on Data Mining. Piscataway: IEEE Press, 2020: 1118-1123. [29] GOLDSTEIN M, DENGEL A. Histogram-based outlier score (HBOS): a fast unsupervised anomaly detection algorithm[C]//Proceedings of the KI-2012 35th Genman Conference on Artifical Intelligence. Saarbrücken: Springer, 2012. [30] ZENATI H, ROMAIN M, FOO C S, et al. Adversarially learned anomaly detection[C]//Proceedings of the 2018 IEEE International Conference on Data Mining. Piscataway: IEEE Press, 2018: 727-736. -







 下载:
下载: