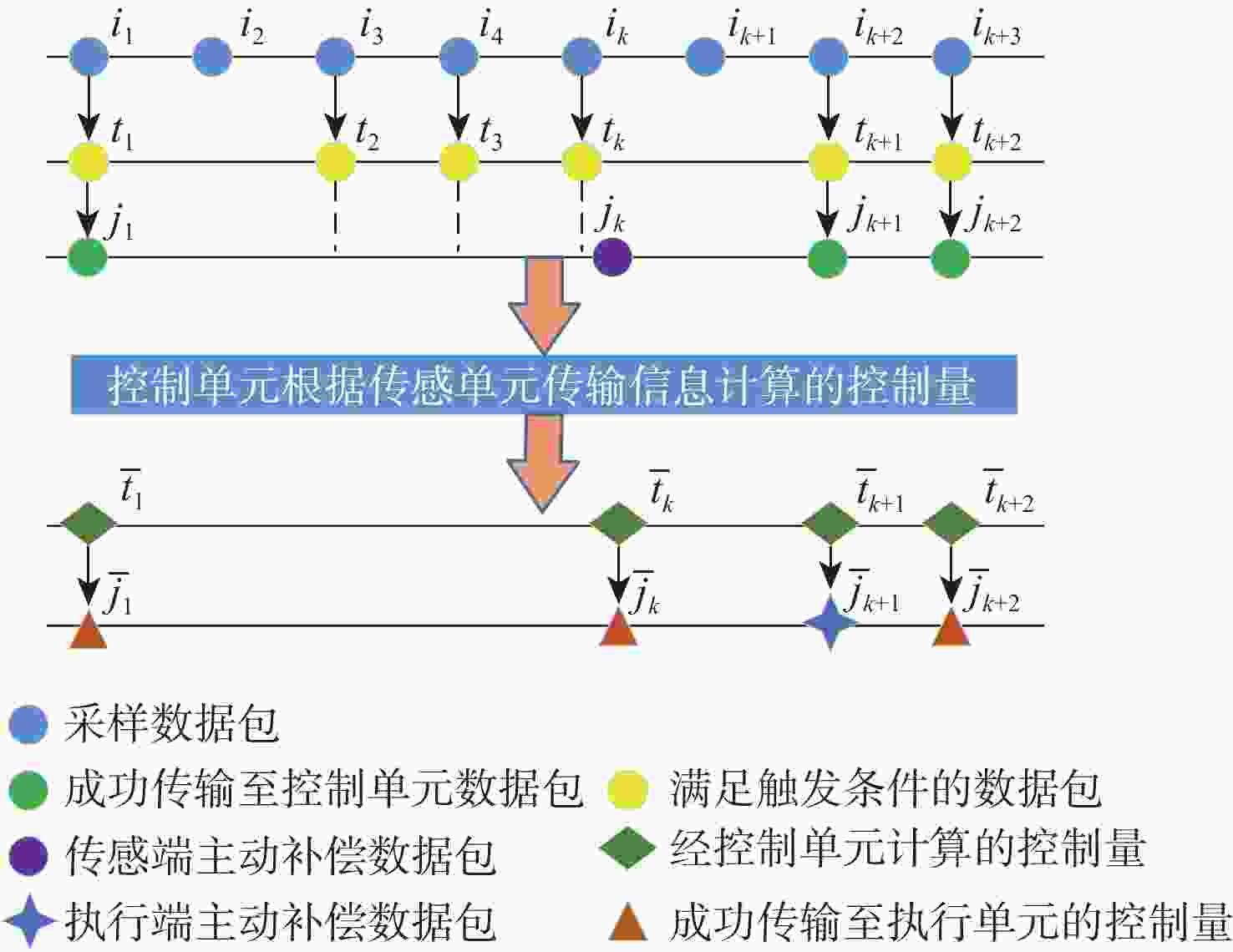
ICPS multi-modal integrated security control based on data-model linkage under dual-end asynchronous DoS attacks
-
摘要:
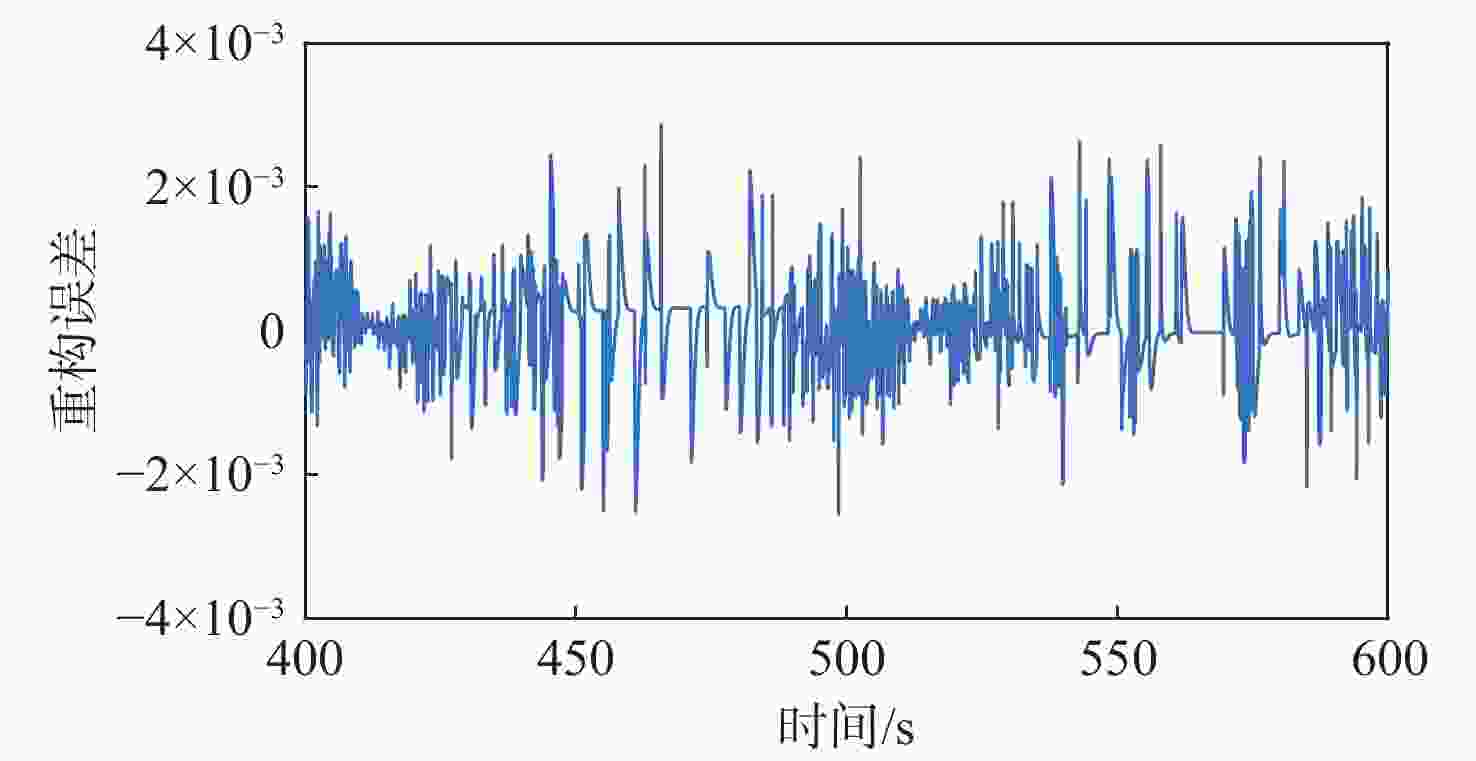
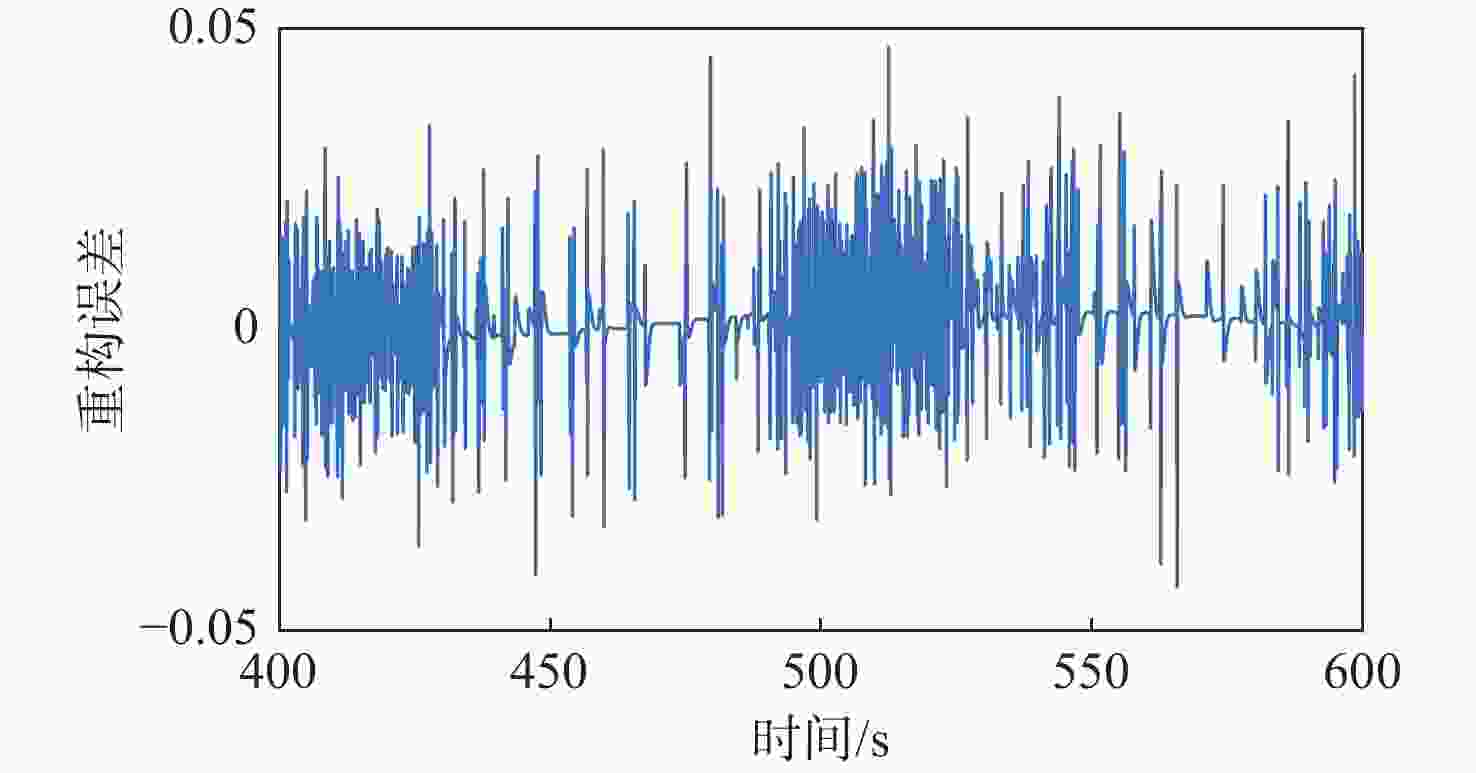
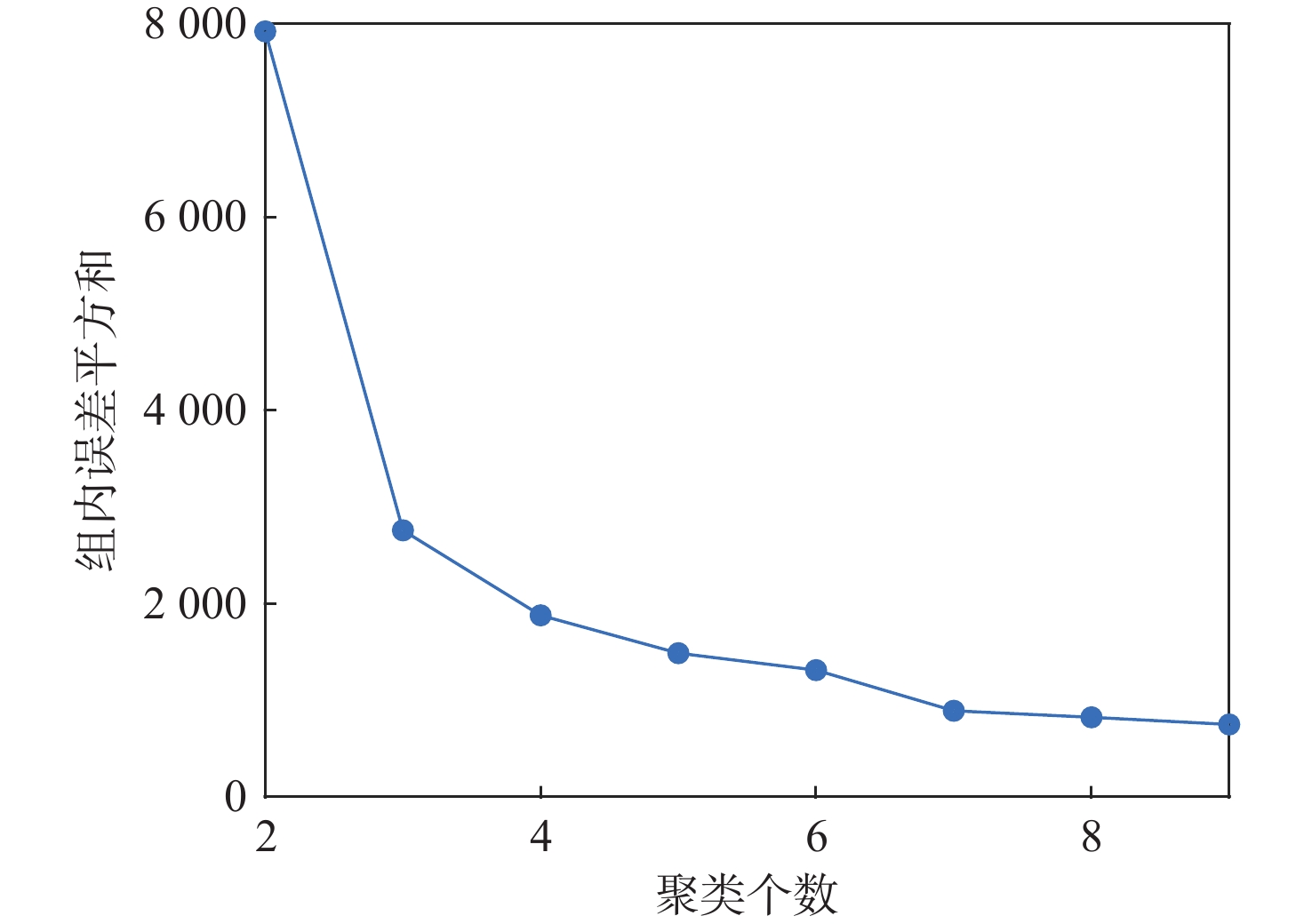
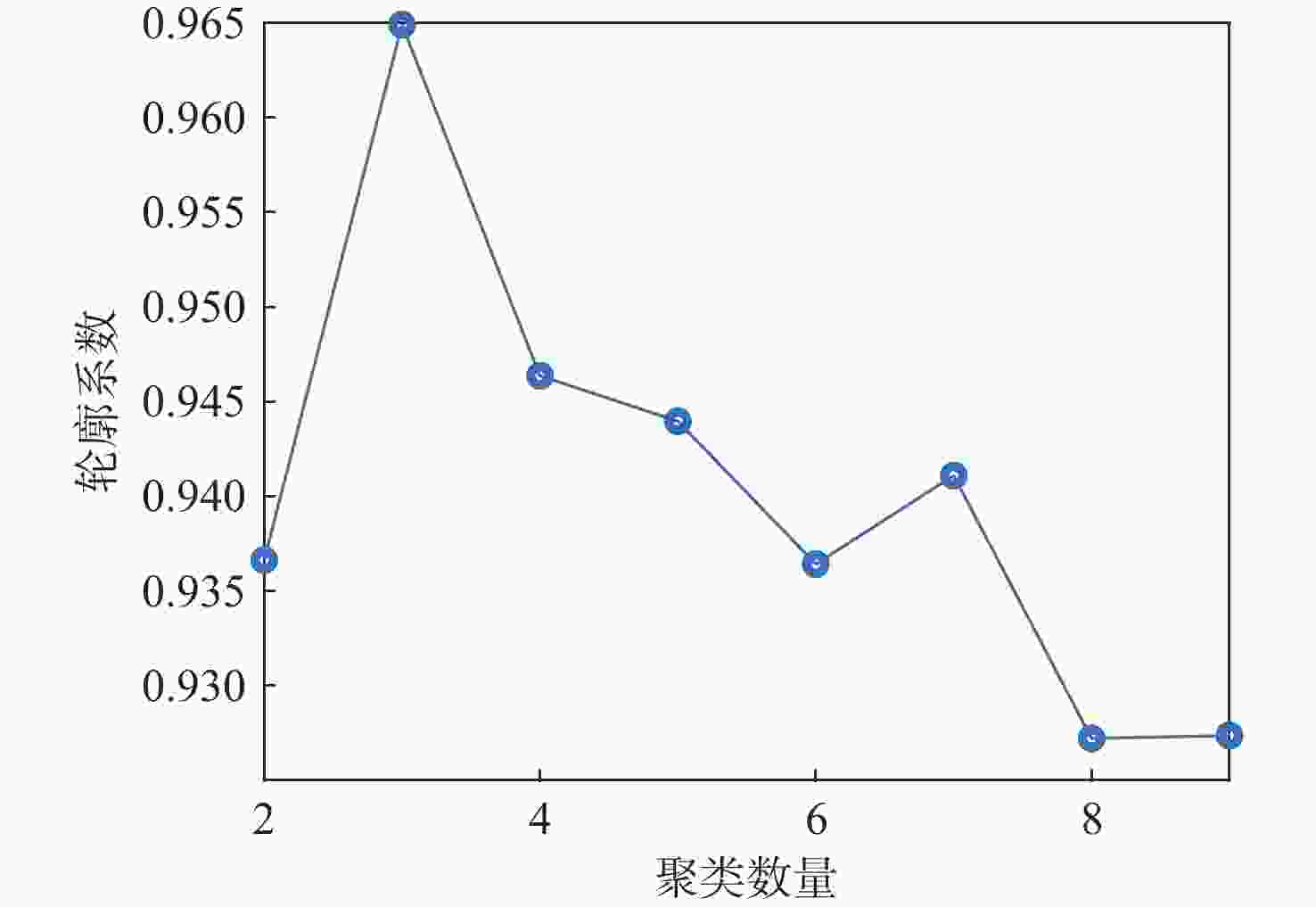
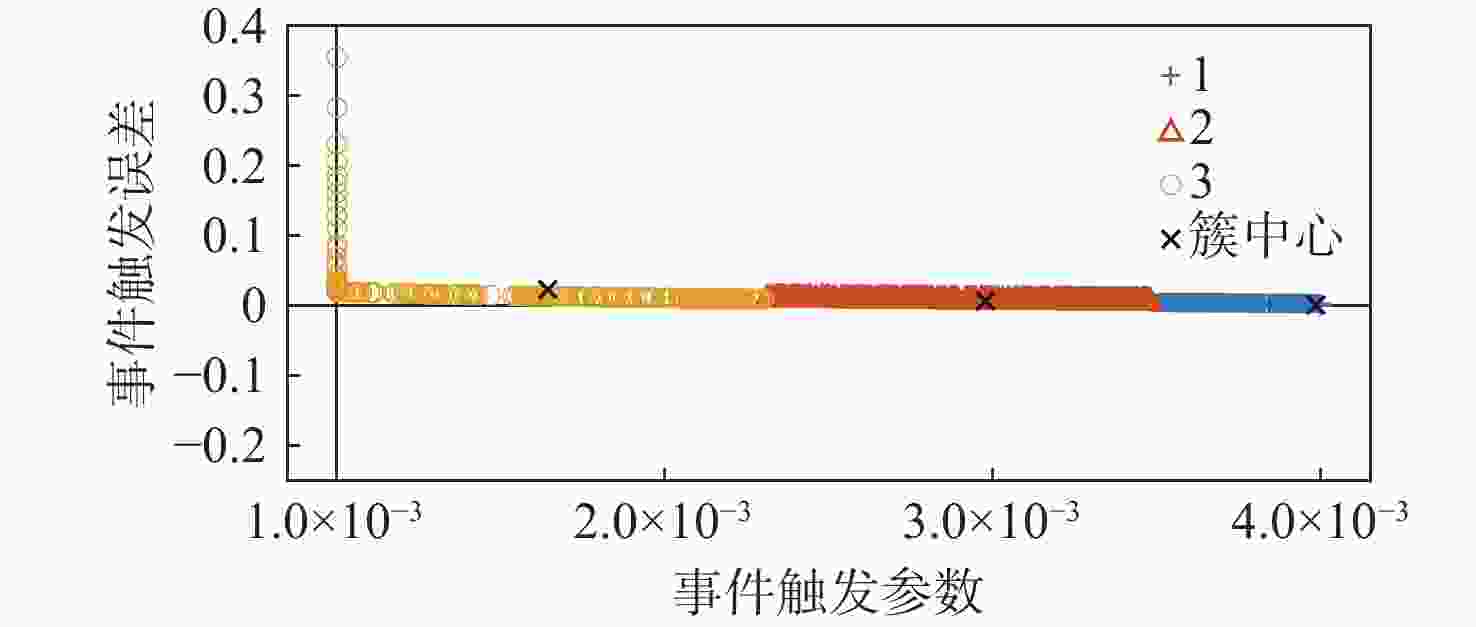
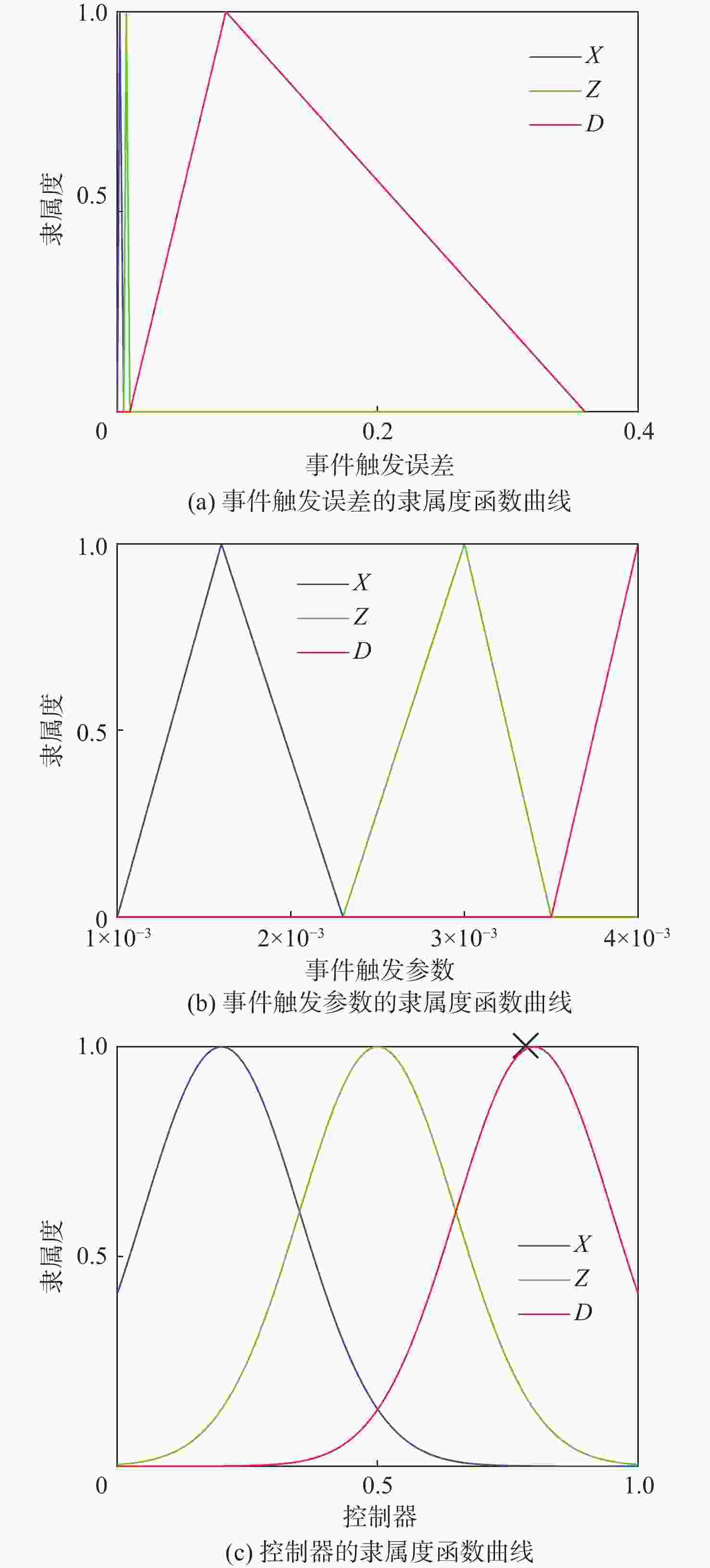
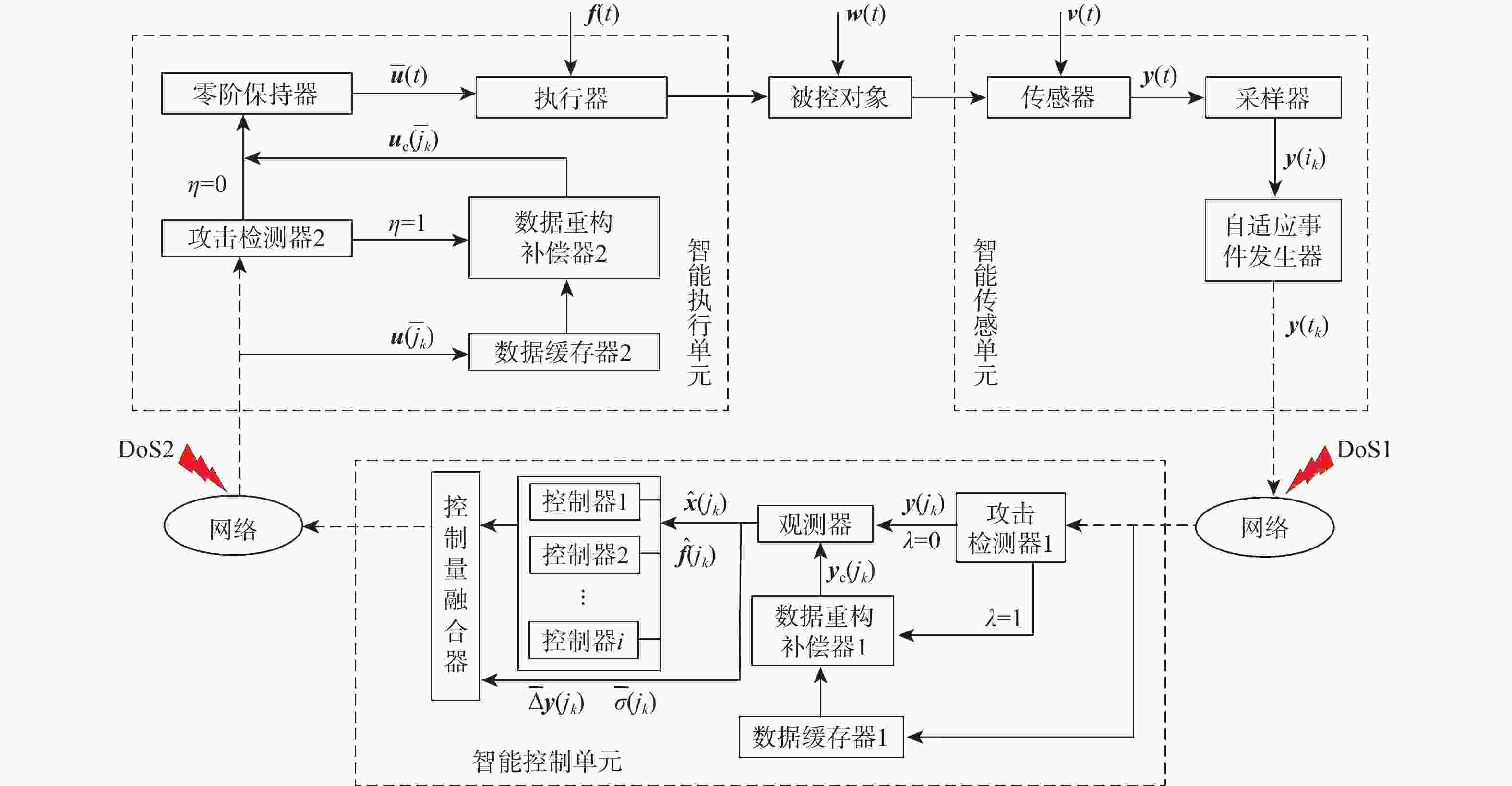
针对一类双端异步拒绝服务(DoS)攻击与执行器故障共存的工业信息物理系统(ICPS),通过将数据驱动技术与模型机理解析方法相融合,对多模态综合安全控制与通讯间的协同设计问题进行研究。设计一种触发阈值可随系统行为动态变化的自适应离散事件触发通讯机制(ADETCS),并构建可同时抵御双端异步DoS攻击与执行器故障的ICPS多模态综合安全控制架构;针对不同能量等级的DoS攻击,采用“分而治之”的思想,借助长短期记忆(LSTM)网络与弹性控制方法,提出基于数模联动的主-被动协同混合容侵策略。基于Lyapunov稳定性理论进行观测器与控制器的推证,进而采用K-Means++聚类算法及模糊融合方法,在线对不同模态下的控制器进行加权融合,实现不同控制模态间的软切换;通过四容水箱实例,验证了双端异步DoS攻击下基于数模联动的多模态综合安全控制方法的正确性。实验结果表明:数模联动的方法增强了ICPS抵御双端异步DoS攻击的能力,多模态综合安全控制器的设计实现了控制模态与ADETCS间的双向自适应协同控制。
-
关键词:
- 工业信息物理系统 /
- 双端异步DoS攻击 /
- 数模联动 /
- 自适应离散事件触发通讯机制 /
- 多模态综合安全控制
Abstract:Data-driven technology and model mechanism analysis techniques are combined to study the problem of multi-modal integrated safety control and communication collaborative design, with an eye toward a type of industrial cyber-physical system (ICPS) that is susceptible to dual-end asynchronous denial of service (DoS) attacks and actuator failures. Firstly, an adaptive discrete event triggered communication scheme (ADETCS) with a trigger threshold that can dynamically change with the system behavior is designed, and an ICPS multi-modal integrated safety control architecture that can simultaneously resist asynchronous dual-end DoS attacks and actuator failures is constructed. Secondly, an active-passive collaborative hybrid intrusion tolerance strategy based on data-model linkage is proposed. Then, combined with the idea of “divide and conquer”, a tolerance method for dual-end asynchronous DoS attacks is proposed with the help of a long short-term memory (LSTM) networks and elastic control. Thirdly, the observer and controller are deduced based on Lyapunov stability theory, and then the K-Means++ clustering algorithm and fuzzy fusion method are used to perform weighted fusion of controllers under different modes online, thus realizing soft switching between different control modes. Finally, the effectiveness of the proposed method is verified through a four-tank example. According to the experimental results, the data-model linkage method improves ICPS's resistance to dual-end asynchronous DoS attacks, and the multi-modal integrated safety controller's design enables two-way adaptive cooperative control between the ADETCS and control mode.
-
表 1 不同控制模态下的参数
Table 1. Parameters under different control modes
模态 $ \bar \sigma ({t_k}h) $聚类中心 $ {e_y} $聚类中心 $ \bar \sigma ({t_k}h) $范围 $ {e_y} $范围 $ {C_1} $ 0.004 0.0019 ( 0.0035 ,0.004)(0,0.005) $ {C_2} $ 0.003 0.0069 ( 0.0023 ,0.0035 )(0.005, 0.0097 )$ {C_3} $ 0.0016 0.00234 (0.001, 0.0023 )( 0.0097 ,0.36)表 2 模糊规则
Table 2. Fuzzy rules
$\sigma ({t_k}h)$ $\Delta \bar {\boldsymbol y}({j_k})$ D Z X D D/D D/Z D/X Z Z/D Z/Z Z/X X X/D X/Z X/X -
[1] WU Y Y, ZHANG L W, XIE W, et al. Robust mixed H2/H∞ model predictive control for cyber-physical systems with input saturation and energy-bounded disturbance[J]. IEEE Transactions on Industrial Informatics, 2024, 20(6): 8328-8337. doi: 10.1109/TII.2024.3372036 [2] 薛威峰, 孙子文. 数据注入攻击下ICPS的自适应事件触发弹性控制[J]. 控制理论与应用, 2024, 41(5): 866-874. doi: 10.7641/CTA.2023.20774XUE W F, SUN Z W. Adaptive event triggered resilient control of ICPS under data injection attack[J]. Control Theory & Applications, 2024, 41(5): 866-874(in Chinese). doi: 10.7641/CTA.2023.20774 [3] JI Z D, CHEN C L, HE J P, et al. Edge sensing and control co-design for industrial cyber-physical systems: observability guaranteed method[J]. IEEE Transactions on Cybernetics, 2022, 52(12): 13350-13362. doi: 10.1109/TCYB.2021.3079149 [4] ZUO F L, LUO Z X, YU J Z, et al. Vulnerability detection of ICS protocols via cross-state fuzzing[J]. IEEE Transactions on Computer-Aided Design of Integrated Circuits and Systems, 2022, 41(11): 4457-4468. doi: 10.1109/TCAD.2022.3201471 [5] 梁宏, 刘佳男, 李勇. “火焰” 病毒分析与防范[J]. 信息网络安全, 2012, 12(8): 157-159.LIANG H, LIU J N, LI Y. Analysis and protection of flame virus[J]. Netinfo Security, 2012, 12(8): 157-159(in Chinese). [6] YANG H Q, LI T S, LONG Y, et al. Event-triggered distributed secondary control with model-free predictive compensation in AC/DC networked microgrids under DoS attacks[J]. IEEE Transactions on Cybernetics, 2024, 54(1): 298-307. doi: 10.1109/TCYB.2022.3218026 [7] YANG F S, LIANG X H, GUAN X H. Resilient distributed economic dispatch of a cyber-power system under DoS attack[J]. Frontiers of Information Technology & Electronic Engineering, 2021, 22(1): 40-50. [8] 彭大天, 董建敏, 蔡忠闽, 等. 假数据注入攻击下信息物理融合系统的稳定性研究[J]. 自动化学报, 2019, 45(1): 196-205.PENG D T, DONG J M, CAI Z M, et al. On the stability of cyber-physical systems under false data injection attacks[J]. Acta Automatica Sinica, 2019, 45(1): 196-205(in Chinese). [9] GONG Z Y, YANG F S. Secure tracking control via fixed-time convergent reinforcement learning for a UAV CPS[J]. IEEE/CAA Journal of Automatica Sinica, 2024, 11(7): 1699-1701. doi: 10.1109/JAS.2023.124149 [10] 张正道, 杨佳佳, 谢林柏. 基于辅助信息补偿和控制信号编码的重放攻击检测方法[J]. 自动化学报, 2023, 49(7): 1508-1518.ZHANG Z D, YANG J J, XIE L B. Replay attack detection method based on auxiliary information compensation and control signal coding[J]. Acta Automatica Sinica, 2023, 49(7): 1508-1518 (in Chinese). [11] 杨中林, 魏自航, 林相泽. 线性系统的事件触发输出反馈有限时间有界控制[J]. 控制理论与应用, 2022, 39, (8): 1497-1505.YANG Z L, WEI Z H, LIN X Z. Event-triggered output feedback finite-time bounded control of linear systems[J]. Control Theory and Applications, 2022, 39, (8): 1497-1505(in Chinese). [12] 陈烁, 樊渊. 基于采样的线性不确定系统事件触发控制[J]. 控制工程, 2021, 28(5): 999-1004.CHEN S, FAN Y. Sampling-based event-triggered control for linear uncertain systems[J]. Control Engineering of China, 2021, 28(5): 999-1004(in Chinese). [13] HUANG S, ZONG G D, XU N, et al. Adaptive dynamic surface control of MIMO nonlinear systems: a hybrid event triggering mechanism[J]. International Journal of Adaptive Control and Signal Processing, 2024, 38(2): 437-454. doi: 10.1002/acs.3708 [14] ZHAO C H, SHEN Y J, PANG H X. Adaptive output-feedback control for switched nonlinear systems with measurement sensitivity based on double-side event-triggering mechanisms[J]. International Journal of Systems Science, 2024, 55(11): 2349-2372. doi: 10.1080/00207721.2024.2344036 [15] FRIDMAN E. A refined input delay approach to sampled-data control[J]. Automatica, 2010, 46(2): 421-427. doi: 10.1016/j.automatica.2009.11.017 [16] HOCHREITER S, SCHMIDHUBER J. Long short-term memory[J]. Neural Computation, 1997, 9(8): 1735-1780. [17] ZHANG X M, HAN Q L, SEURET A, et al. Overview of recent advances in stability of linear systems with time-varying delays[J]. IET Control Theory & Applications, 2019, 13(1): 1-16. [18] ZHANG X M, HAN Q L. Global asymptotic stability analysis for delayed neural networks using a matrix-based quadratic convex approach[J]. Neural Networks, 2014, 54: 57-69. doi: 10.1016/j.neunet.2014.02.012 [19] ARTHUR D,VASSILVITSKII S.K-means++: the advantages of careful seeding[C]//Proceedings of the 18th Annual ACM-SIAM Symposium on Discrete Algorithms.New York: ACM, 2007:1027-1035. [20] 邱爱兵, 吉虹钢, 顾菊平. 非均匀采样数据系统时变故障估计与调节最优集成设计[J]. 自动化学报, 2014, 40(7): 1493-1504.QIU A B, JI H G, GU J P. Optimal integrated design of time-varying fault estimation and accommodation for nonuniformly sampled data systems[J]. Acta Automatica Sinica, 2014, 40(7): 1493-1504(in Chinese). [21] 李炜, 韩小武, 李亚洁. 基于DoS攻击能量分级的ICPS综合安全控制与通信协同设计[J]. 信息与控制, 2022, 51(3): 257-270.LI W, HAN X W, LI Y J. Co-design of integrated security control and communication of ICPS based on DoS attack energy classification[J]. Information and Control, 2022, 51(3): 257-270(in Chinese). [22] 程雪. ADETCS下ICPS多模态综合安全控制与通讯协同设计[D]. 兰州: 兰州理工大学, 2023: 42-50.CHENG X. Collaborative design of multimodal integrated safety control and communication of ICPS under ADETCS[D]. Lanzhou: Lanzhou University of Technology, 2023: 42-50(in Chinese). [23] PENG C, ZHANG J, YAN H. Adaptive event-triggering load frequency control for network-based power system[J]. IEEE Transactions on Industrial Electronics, 2016, 63(8): 1685-1694. doi: 10.1109/TCYB.2017.2659698 -






 下载:
下载: